Some of you will know what I'm talking about.
For others ( who don't like to follow links ), Vim is a text editor and GPG is public key encryption software.
Text editors just edit text; there's not much in the way of layout options, but they're very good at manipulating text in interesting ways. Vim is a favorite of mine since I find it quite powerful and it's available for just about every platform I work on.
Public key encryption software is a bit more complicated. At it's core, it's way to use encryption between two people who've never met. A very simplistic analogy is a box with two keys; one locks the box, the other unlocks it if it was locked with a particular lock key. These boxes are universally available, for free.
When you want to communicate securely, you first go to the box dealer and get two keys ( one that locks any box and one that unlocks boxes locked with the first key ). You give the lock key to all your friends and encourage them to give it to their friends. You even hang a copy of your lock key on the bulletin board of the coffee shop you hang out in from time to time.
Now, someone wants to send you a message and they don't want anyone else to read it. First, they go to the box dealer and get a box. Then, they take a copy of your lock key ( say, the one you hung in the coffee shop ) , put the message in the box and lock it with your lock key.
Since these keys come in pairs, their own unlock key doesn't work. No one else's does either; to unlock the box, you have to use the unlock key that corresponds to the lock key.
This someone now mails the locked box to you as they would anything else.
You get the box, perhaps delivered with some catalogs, bills, and other junk mail. You take out your unlock key and unlock the box, then read the message.
In this example, the "lock" key is called a public key, the "unlock key" is a secret key, and boxes are the GPG program. Sending the box is email, but the transport method isn't that significant.
With me so far? Ok. So, I wanted to use my favorite text editor to write a message without leaving any traces on my computer and GPG it.
First, I invoked Vim with this command from a command prompt:
gvim -n
The "-n" bit says "don't write anything to the hard drive unless I tell you to". Perhaps you might think that most programs don't write anything to the hard drive unless you tell them to, but that's not always the case. In Vim's case, it opens a "swap file" whenever it's invoked. It does this so if something bad happens while you're using it there's a chance the data is still recoverable.
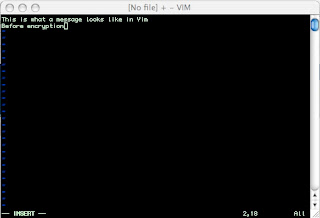
Usually this is a good thing, but when you want to send something only your intended recipient can read it's not a good idea to leave unencrypted data laying around. People would have a very hard time breaking GPG, but they don't have to if you're going to leave the message for anyone to find.
So, with Vim open, I type my message. Once done, I enter the command:
:%! gpg -q -e -a -s -r
Whoa. WTF is that??
Ok, the ":%!" says "take the stuff I just typed and send it the application I'm specifying next". The application, in this case, is GPG. The options to GPG break down like this:
-q = quiet mode. Just do what I tell you and shut up about it.
-e = encrypt.
-a = ascii output. In other words, make the output consist of letters, numbers, and a few symbols that are safe to send in the body of an email message.
-s = sign it. Digitally, this is optional but allows someone with your public key to check to ensure it's really you that sent the message.
-r = recipient. Who gets this, specified by email address.
A prompt pops up, asking for my GPG pass phrase. I enter it and the contents of my Vim window are replaced with the ASCII encoded encrypted message. From there, it's a simple cut-and-paste into the email body.
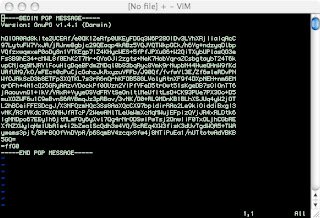
Once that's done, I exit Vim with:
:q!
Which means "Close Vim, abandon everything I just did and yes I really mean it so don't ask". Since there was no swap file generated on opening, there's no trace left on the machine of the text you wrote; only the encrypted version remains.
No comments:
Post a Comment